DEVSECOPS CONSULTING SERVICES
Integrating ‘Security as Code’ Culture within DevOps
Overview
Enterprise computing has recently seen a considerable transition as a result of DevOps adoption. With the use of features like serverless computing, dynamic provisioning, and pay-as-you-go cost models, DevOps methods help enterprises get a number of value-added benefits, including enhanced agility, speed, and cost reduction.
DevOps has been found deficient in situations requiring the secure delivery of code, despite the fact that it is extremely popular. As a result, a novel strategy known as “DevSecOps” was created, which makes it easier for information security and DevOps to coexist.
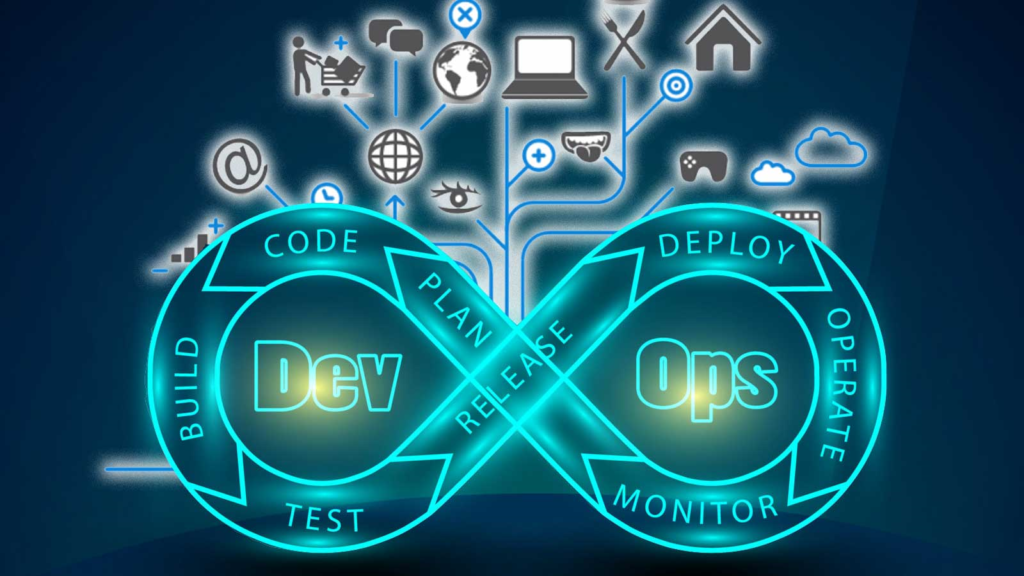
Our Offerings
DevSecOps
- DevSecOps entails integrating the security component into the DevOps process
- DevSecOps products are focused on solving security problems related to DevOps Automation, including composition analysis and configuration management
DevOps
- DevOps refers to the collaborative atmosphere between the development, testing, and operations teams to accomplish continuous delivery.
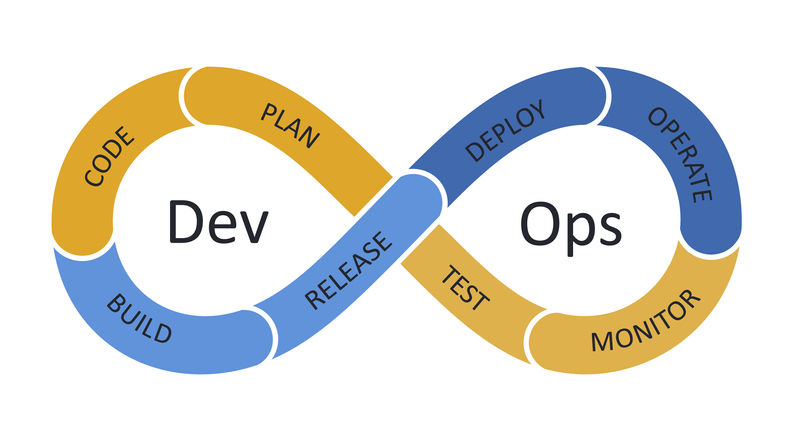
Approach for DevSecOps
To more effectively combat real-time security risks, organisations must adopt a cultural and technical transformation in their approach to DevSecOps services.
Six key elements must be taken into account for a practical DevSecOps approach. They consist of:
Analysis of code
By delivering code in manageable portions, this enables the speedy detection of vulnerabilities.
Change management
The ability to submit modifications that can increase speed and efficiency as well as determine whether the change will have a positive or negative impact is provided by change management.
Monitoring compliance
Organizations should follow regulations like the Payment Card Industry Digital Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR) and be prepared for audits at any moment from the authorities.
Investigating Danger
Each code update is accompanied by a list of potential new threats. It’s critical to identify these risks as soon as you can and to act right away.
Vulnerability Assessment
This process entails identifying fresh vulnerabilities and determining how to address them.
Training
Companies should provide their software and IT engineers with security-related training and arm them with the rules for predetermined procedures.
Approach for DevSecOps

Mandating security at all times

Complete evaluation before security

Changes to the code that are security-related Automation of all possible procedures

Monitoring ongoing activity using dashboards and alerts

